Industries Served
INTEGRATED SECURITY SOLUTIONS
INNOVATIVE SECURITY TO CREATE A SAFER WORLD FOR FUTURE GENERATIONS.

INDUSTRY SOLUTIONS
Security Management Systems:
Condortech Services, Inc. has more than 30 years of experience working the Federal and Government agencies. We are Homeland Security Presidential Directive 12 (HSPD-12) compliant, proven to help with your HSPD-12 programs. Our key focus is in the Personal Identity Verification (PIV) system, supported by a common smart card-based platform for identity authentication and access to multiple types of physical and logical access environments. CTS, being a security system integrator, has taken a step further by looking at other directives to provide a unifying framework that integrates a range of efforts designed to enhance the safety of our Nation’s critical infrastructure, as issued by the National Infrastructure Protection Plan in 2009. The success of implementing systems of systems that will adapt to the security system at your facilities has always been with the use of at least 50-66% of the existing legacy system, such as PACS.
CTS systems have passed the many tests and evaluations by the Department of Commerce (NIST CRADA) and the General Services Administration (GSA), and can offer these services to Federal and Government agencies.
1. Comprehensive Security Systems with Design-Build and Installation
- Objective: design-build of security projects to facilitate the implementation of a security system which meets all identified needs by integrating socio-economic factors and cultural-impacts into the overall security solution.
- Our “Systems of Systems” includes various solutions from smart card readers to smoke alarms, which are energy efficient and full compliant with different government regulations and initiatives.
- Areas targeted: Border, Maritime, Airport, ITS, Health Care, Educational Facilities, Defense and Homeland, Emergency Evacuation Systems, and Infrastructure Security; to name a few.
2. Central Command, Communications & Control (C4) System with Redundant and Interoperable Capabilities
- Objective: Allows the integration of cameras, intrusion detections, biometric systems, communication systems, perimeter protection systems, and access control systems into one Control Center.
- Our “Systems of Systems” is the result of the C4, providing the understanding of the security staff’s culture and environment. It uses wireless communication for mobile units that can monitor areas in a certain infrastructure.
3. Information Security and Audio Countermeasures
- Objective: Providing services and experts for the detection and elimination of electronic-information security leaks in communication and computer systems.
- Our sophisticated electronic “sweeping techniques” help us neutralize and prevent industrial espionage and electronic eavesdropping, with no disruption to the client’s business operations.
- Technology used: Microelectronics and undetectable voice and hearing devices
4. Asset Tracking Management Systems Design
- Objective: Track the Where, When, and Now of Asset Logistics and Control with Radio Frequency Identification (RFID) technology.
5. The Biometric Solution
- Objective: Identify and verify individuals based on their physical or behavioral characteristics through computerized methods that use real time databases.
- Technologies used: Fingerprint, face, hand geometry, iris, palm prints, signature, and voice.
- 3 Step process that can operate in two distinct modes (Authentication and Identification)
6. ID Management and Card Management Systems
- Objective: Provide efficient storage, retrieval, and manipulation of digital images, text, and graphic information with a multi-media management system solution using software design and hardware components compliant to HSPD-12.
- CTS is capable of meeting any organization’s growing security needs with this powerful system.
7. Smart Card System
- Objective: To offer enhanced security through encryption and mutual authentication through a user-friendly, affordable, and reliable multi-functional ID card protected with DES or triple DES encryption security.
- Functions: PIV card, PKI Certificates, Sports Access Card, Door access, logical access, etc.
- Compliance standards: 15693, 14443A, 14443B2
8. Physical Access Control System (PACS) with Design-Build and Support
- Objective: Provide an overview of the movements of personnel in an entire organization’s facility and produce detailed reports of whereabouts and supervision
- Functions:
- Unix, Linux, or Windows OS based-access control system connected through LAN/WAN Networks
- Multi-tasking/user software
- Integrates with other systems (Intrusion, biometrics, CCTV, ID Mgmt.)
- Flexible to grow and expand to accommodate long-term needs.
- Its intelligent controller supports multiple card technologies such as proximity, magnetic stripe, contact-contactless smart cards, bar code and others.

Cloud Computing:
- About the Cloud: A centralized information system with less servers thus reducing power, energy, and space; creating an interoperable environment with a unified management of its services.
- CTS’ Cloud Computing Services (CSS): Our Private Cloud is used by most local governments, educational facilities, and federal agencies and has Citrix or Vmware as an Operating System.
Your business will be less susceptible to Cyber Attacks with our proven sensor technology, strong hardware and software support of Cloud Computing along with different Electronic Security Sensors.

Our Global Cloud Solutions Providers:
- Stratus Technologies is focused on helping customers achieve and sustain the availability of information systems that support their critical business processes. Offers many technologies and support services for Small to Mid-Size businesses such as Avance Software 2.0, a rigourous and comprehensive system that imports/exports, backs-up/restores data, making it easier to integrate it into existing IT infrastructures.
- VMware is one of the global leaders in cloud infrastructure, delivering customer-proven virtualization solutions that significantly reduce IT complexity. Its first vSphere OS, enables organizations to consolidate servers and storage, resulting in reduced IT hardware, maintenance costs, energy costs, improves operational flexibility and reduces real estate costs. They accelerate the transition and preserve existing IT investments, enabling more efficient service delivery without compromising control.
- Technical Considerations: Software recommended by CTS will be solid and there will not be a need to customize anything, all sensors and security applications are off the shelf with proven technology in other Cloud and non-Cloud environments. CTS also has configured Servers with the necessary storage space and the data to be transmitted in minimum based on the amount of card readers and micro-controllers.
We provide various applications and servers to have the optimum appliance-based solutions to configure and deliver/retain data at the best possible rate and speed.
This diagram illustrates a Security System on a Private Cloud:
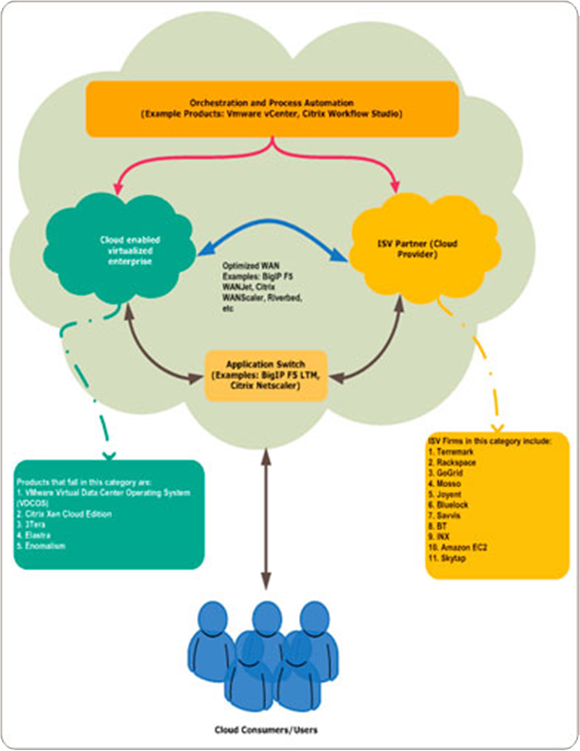
This diagram illustrates a Security System on a Private Cloud:
Security Audits and Vulnerability Studies:Conducted by CTS of public and commercial facilities and buildings for threat analyses to determine the type and level of external and internal threats. CTS also conducts an extensive assessment of technical, procedural and personnel capabilities and effeectiveness in order to design security plans, systems, procedures, programs, and responses.
Cyber Security Audits:CTS conducts audits of computer facilities in both private and public sectors in order to determine the necessary measures to insure proper security for handling and processing different levels of sensitive information.
In the Federal Government, this includes the review, evaluation, and implementation of appropriate Federal Regulations regarding computer information.
CTS also develops programs that address both the physical and logical security of the computer and network system. Depending on the vulnerabilities, a combination of logical and encryption systems are implemented. Our Security Engineer’s experience includes the design and supervision of the installation of security systems and programs for computers, communications and peripherals.

Disaster Response Planning:
CTS is here to help you with the necessary preparations in the face of any climate, social, and hazardous threat. CTS works with two emergency plans, Continuity of Operations (COOP) and Continuity of Government (COG), based on federal guidance and best practices in emergency management and continuity planning.
COOP programs build upon existing programs for critical infrastructure protection, business continuity, and (computer) disaster recovery planning. CTS will help you design an integrated COOP to ensure a command and control response and recovery operations as well as continuance of basic governmental functions with minimum disruption.
Some objectives of COOP plan include:
Ensuring continuous performance of essential function/operations during an emergency
Protecting facilities, equipment, record, and other assets
Reducing or mitigating disruption to operations, loss of life, and other losses
Achieving a timely and orderly recovery from an emergency
Some functions of an effective COOP program:
- Plans and Procedures
- Delegations of Authority
- Orders of Succession
- Communications and Warning
- Protection of Vital Records and Databases
- Testing, Training, and Exercises
- Roles and Responsibilities
- Mitigation and Countermeasures
- Command and Control
Our Solutions:
Private Turn-Key Data Centers: Strategically located centers in natural disaster-free zone in Virginia, Seattle, and Washington. CTS offers single racks to private cages, custom built, with 100% facility and network uptime to store your data.
Benefit from our data centers, don’t risk losing your data and ability to function during and after an emergency!
For more information on Comprehensive Emergency Management Programs please to go to: http://www.davislogic.com/CEMP.htm

Intelligent Transportation Systems (ITS):
ITS is one of CTS’s leading edge technology, providing information and communication technology applied to transport infrastructure and vehicles that improve transport outcomes such as transport safety, productivity, travel reliability, informed choices, social equity, environmental performance and network operation resilience.
Technologies applied: Car navigation, traffic signal control systems, container management systems, variable message signs, automatic number plate recognition, security CCTV system, parking guidance and information systems, weather information, bridge deicing systems; etc.
Targeted Areas: Traffic Control, Surveillance and Monitoring of Vehicles and Assests, Security for Streets
Features: Software, Hardware, Sensing Technologies, High Speed Readers, Wireless Communications, Loop Detectors, Microcontrollers, Fiber Optics, Routers, RFID Technologies, etc.; integrated into one “System of Sytems” for immediate response from the Command Control Center.

