Blog
BLOG
Talent Needed!
As an executive, one of my biggest headaches is finding and hiring talent. Other integrators have felt the same gap of skills and the few specialized engineers available come at a high price. I knew my headache was legitimate when I saw Bloomberg’s report yesterday (Jan 24th), that the United States has fallen out of the Top 10 Countries for Innovation. Meanwhile, Israel ranked # 10 and South Korea remained #1.
Back in 2015, Forbes listed out the Top 10 Countries with the Most Engineering Graduates. Three years ago, we were in second place with 237,826 graduates a year. #1 was Russia, with twice as many engineers. I did not locate an updated, reliable report; however, if our engineer graduates remained the same or increased, then bodies aren’t the issue. Why aren’t we innovating like we used to? The genesis lies in our educational system.
Security, as I explained in my previous article, is a multi-discipline area; highly specialized. It requires hands-on training. When we hire a new graduate from impressive school X we find ourselves training him for 9-12 months before he is able to go out into the field and produce on his own. Some training is expected, but it points to a deficiency in the educational system.
moreHolistic Security
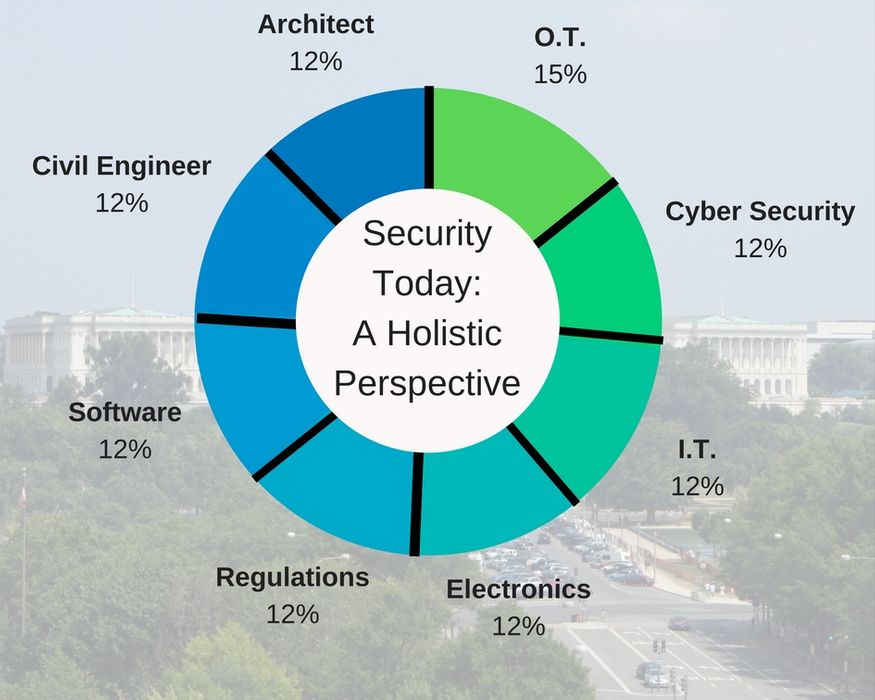
2018 marks 28 years for Condortech Services. Starting from my basement, I am really humbled by the progress we’ve made in these past few decades. The reminiscing didn’t last too long though; I really started to reflect on the industry as a whole and how I’ve seen it evolve over time. When we started in my basement, security was a one-horse kind of industry. You installed a camera, a badge reader for entry and you got a gold star. As I am forecasting my company’s future, I realize security integrators must rise to the level of 360° risk mitigators. The origin of this holistic shift stems from a smarter customer, but also from the sophisticated threats we see reported everyday by the media.
There are 8 major components every integrator (and end user) needs to understand and hopefully master. These include: Architecture, Civil Engineering, Cyber Security, Information Technology, Electronics, Government Regulations, Software, and Operating Technologies.
Architecture: When the client asks for a design-build system, the keys are in your hand. Whether it’s for a condominium complex or a military base, they want something aesthetically pleasing. There is a lot to be said about a lobby that looks beautiful, and yet is fully secured. Making sure you have capable people to draw, design and envision will put you ahead of the competition.
moreProperty Management: Security Systems Add Ease
Managing an apartment complex with a single uniform security system is complicated enough; managing a business park, mall, or other structure with multiple businesses and security needs is in a league all its own. Do you need to zone security by building? By floor? By office space? If you don’t know your way around security system specifics, setting up a sufficient and functional security system for your property and tenants’ needs can be a months-long headache. And, in the end, the security system may or may not cover every security concern! Instead of fighting through on your own, trust the security system experts to protect your property. The team at Condor Tech here in Washington D.C. take the time to design a security system individually for each of our clients, so we can put in place the technology that will best benefit your properties and your tenants.
ACCESS CONTROL
As property managers, it’s ultimately up to you to control who has access to your buildings. This can be complicated when you have a number of different tenants and staff accessing different buildings – or even different portions of a building or floor – because each business is going to have their own security needs. One of the primary steps to efficient security is to control access to every area. Depending on security needs, this can be done through security badges that must be scanned or swiped at access points. These access points can be as broad as opening a gate to the complex and get as specific as entry to a single floor or room. To provide added protection, restricted areas can require additional security measures, such as codes or biometric screening. When you work with Condor Tech, we can customize zones based on the security you and your tenants need.
moreSecuring Your Startup With The Right Security System
High-tech startups aren’t restricted to Silicon Valley any longer. With widespread access to technology and the easy access to idea-sharing programs online, it seems like technology-centric startups are popping up across the country. If you have a brilliant idea but lack the technological know-how to actually make it happen, it’s easier than ever to team up with someone across the country who is willing to take a leap of faith on your idea. However, as any tech-based movie will tell you, having ample security is important to protecting your magnificent creation from theft, either physical or digital.
HIGH-TECH SECURITY SOLUTIONS
Well, okay, maybe those movies about digital information theft may be more than a bit dramatically overblown, but they convey the idea about the need for digital security pretty thoroughly. Unfortunately, protecting your business digitally isn’t quite as straightforward as hiring a few security guards and installing a security camera system – although, you may want to take those measures as well. When it comes to protecting yourself digitally, a locked door and a security camera is hardly going to be sufficient to stop a hacker intent on accessing your information. If you are storing the lifeblood of your business digitally, you ought to take sufficient measures to protect that information.
moreHSPD-12: How Is Your ID Management?
How often does science fiction affect the evolution of technology for our world? Think about the communicator used by characters in Star Trek – it’s easy enough to make the leap to modern day cell phone based on shape and function. The Jetsons had a robot maid; we may not have one device that can handle all the household chores, but a Roomba is distinctly a step in the right direction and the various smart home appliances definitely make it possible to have a futuristic home. Then, what about all the security measures that crop up in spy and heist movies? Nearly every workplace with a security concern has probably admired the measures that become capable through acting, imagination, and CGI assistance. Still, there are many security measures seen so commonly in movies that have real-world counterparts that offer just as much protection, if not more.
IMPROVING SECURITY MEASURES
Whether you are in charge of a government entity or simply run a business in which most of your important records are digital, it’s imperative that your security can keep your employees and your data safe. Security solutions to do this can start with more standard measures like installing live and recordable security cameras and/or hiring security guards. However, the more information you have to protect, the more high-tech you’ll need to go for your security solutions. Biometric security solutions can include facial recognition, fingerprint scanning, and even iris identification to greatly increase the control you have over who can access which areas or what information.
moreHiring a Security Firm Versus Independent Security Consultant
If you’re in the process of setting up a new business or just moving to a new office space, your classified information needs to stay that way. Of course, the best way to ensure your information’s security is to have an integrated and comprehensive physical and digital security system that allows you to monitor everything. Granted, your security needs may vary whether you’re in the government sector, healthcare, or something else entirely. Don’t base your security on a straight-from-the-box security surveillance system. To fully protect your information, your security system should be designed and customized to your unique security needs, which means hiring a trained security consultant. The next big option you’ll need to decide between is: Does it matter whether your system is designed by a security solutions firm or an independent security consultant?
INDEPENDENT CONSULTANTS
Hiring an independent security consultant or security advisor is rather similar to hiring an independent architect to design your home rather than going to a home building firm. When you choose an architect to design a new home, you’ll get the individualized attention and drafting that allows you to customize as much as the laws of gravity and physics will allow. This can be a boon for creativity in comparison to the design restrictions placed by a housing development.
moreA Brief History of the Security Camera System
Thanks in large part to George Orwell’s novel Nineteen Eighty-Four, many jokingly or seriously refer to security camera systems as “Big Brother.” This is an impressive legacy for a novel written in 1949, when security camera systems as we know them had barely been a twinkle in developers’ eyes. In Orwell’s novel, the constant refrain, “Big Brother is watching you,” serves as a daunting maxim to the public; thankfully, security cameras are more than just a tool by which authorities exert control. Today, security systems offer protection to your business, information, and employees just as much as they do surveillance.
moreGovernment Contracts for Security Systems
In Washington D.C., government agencies make up a huge majority of the city’s industry. Given that we’re talking about our nation’s capitol, it stands to reason there would be a higher than average amount of government entities here. With so much of our country’s military and government workforce and information here, it is vital that our security systems can keep up with everything being done to run and protect our nation.
moreMake the Most of Your Security System With PSIM
Everyone wants to get the most out of a purchase – whether it’s spending a bit more for shoes that will last you years or investing in software to help you track your business expenses better. In a market where there are countless options available, it’s easier to tailor your purchases to your exact specifications. If you take the time to do this for yourself and your business, why wouldn’t you do the same for your security system?
WHAT IS PSIM?
Part of tailoring your security system involves setting up a physical security information management system (PSIM). This system will allow you to collect and analyze data, quickly verify and resolve any situations that arise, and compile reports and run audits on the system. It’s a one-stop platform that helps you get the most from your security system.
COLLECT AND ANALYZE
Condor Tech’s PSIM software collects data from every layer of physical security you have including security cameras, intrusion detection and access control systems, sensors, and more. It will compile your data into reports so you can analyze any potential issues in your system and prioritize improvements.
moreSecurity Consultants Design the Security World
When you think about bank security, what is the first thing to come to mind? Odds are good you immediately see the two-foot-thick solid steel contraption with the spinning lock made infamous by movies and cartoons. But logically, you know that’s not how your money is protected. There may be a built-in safe involved, but more than likely, your finances are heavily guarded by levels of digital means before the vault is even seen.
MODERN DAY BANK VAULTS
So why should you do differently for your business? You may have the physical components in place, but today, that is rarely enough. A security team to keep watch is an excellent protective step but, as with the bank vault example above, that’s just one element where you should have multiple layers of protection.
At Condor Tech, we are experts at seeing the gaps in any security system. Our security consultants are trained to examine your system for weak spots and create an individually crafted security plan to fit your specific needs. Read on to understand how we differ from your security team.
WHY HIRE A SECURITY CONSULTANT?
Think of it this way: hiring a security consultant is akin to a celebrity hiring a fashion designer to create a dress for the Oscars. A security consultant, at it’s most simple, is a well-trained expert in all varieties of security systems who will tailor your security system to your specific needs. Like that personally designed gown, your security system should fit your business like a glove.
morePerks of Security Cameras
If there is one take-away from the novel and movie The Nanny Diaries, it’s not that New York City’s high society convoluted enough for a soap opera. For our security-conscious readers, the take-away should be centered on the impact a security camera has. When it comes to protecting your family, your home, and/or your business, a security camera system can have a major impact on security.
This may seem common knowledge. The example of The Nanny Diaries might seem overblown, but there’s no way to know what security holes you have until your security system has been analyzed. The security consultants at Condor Tech offer expert services to evaluate and improve your existing system or help you build the best system from the ground up, based on your needs. Read on for some unexpected reasons a security camera system will benefit you!
PREVENT A BAD TEEN MOVIE
With a secure camera system protecting your home, you can deter calamity at home. Think of the damage that could have been prevented in Sixteen Candles if only the Ryan family home was monitored by a camera system. We would have missed out on the epic house party, sure, but no one would have been faced with stacks of empty beer cans and broken furniture when returning from a business trip. With a surveillance system from Condor Tech, you can keep an eye on your house, even whilst you’re out of town, to ensure your teen doesn’t get any wild ideas.
moreBiometric Security: The Perks
When was the last time you saw a security system with biometric protection? For most of us, hand scanners and iris identification are measures straight out of the latest Mission Impossible movie. How will the hero get around the immense protection provided by the eye scanner? Will his face prosthetics be enough to trick the facial recognition software? Sure, it heightens the drama, but that’s the movies! That sort of surveillance system doesn’t actually exist, does it?
When it comes to security systems, biometric measures are no longer the domain of top-secret government facilities and Hollywood spy extravaganzas. At Condor Tech, our state-of-the-art security solutions provide your home or business with the fully customizable security based on your needs. Read on to see how biometrics could enhance your existing security system (or perfect the system of your dreams).
BIOMETRICS ARE THE BEST
One of the biggest worries with any security system is how easily someone could falsify or trick the system to gain access. With biometrics, this is virtually impossible – why do you think these methods are so often the ones used by Hollywood? They seem impossible to defeat because they are the toughest measures available today!
moreSecurity Systems That Support Education
At Condortech, we are aware of the challenging and important work that educators are faced with on a daily basis. There are many problems and distractions that can take away from the ability of teachers and administrators to foster a positive learning environment, and we help to keep these issues to a minimum with security systems tailored to each school’s specific needs. For academic institutions in Springfield and the rest of the country, Condortech provides the resources to make schools safer.
PROTECTING THE NETWORK
Not only do schools depend on a computer network to handle sensitive information for large numbers of students and employees; there is also a high potential for foul play. Students may try to access their school’s network to change grades, while outside threats may target schools to gain access to large quantities of data that could be used for identity theft or worse. Condortech addresses these threats head-on through network engineering and cyber security systems that are proactive to get in front of any potential vulnerabilities.
MAINTAINING A SAFE ENVIRONMENT
moreProactive Vs. Reactive Security
Condortech Services, Inc. is Springfield’s Top Rated Local® security consultant for schools, businesses, government offices, and health care facilities. As such, our top priority is keeping your business or organization safe against any and all threats. One important distinction that should be understood by all of our clients is the difference between proactive and reactive security.
Reactive security means being prepared in the unlikely event of a security breach, either in your network or your physical building. Reactive security measures include the sounding of alarms, sealing off of sensitive areas with automatic locks, and the implementation of contingency plans designed for a specific set of emergency circumstances. Reactive measures are needed to protect your organization when unauthorized individuals have gained access by breaking into the building or hacking your network. They are a necessary piece of any company’s security puzzle, but it would be preferable if those breaches never occurred in the first place.
Proactive security is used to prevent invasions from ever happening in the first place. Automatic access control with sturdy locks that deploy at the touch of a button or on a schedule based on building hours can keep intruders from gaining access to your building. Fortifying windows and identifying potential access points are other ways in which a security consultant can help you to take a proactive approach to protecting your facility.
moreProtect Yourself With Irrefutable Evidence
The administration of Jefferson High School could not have installed a security camera system at a better time. Almost immediately the benefit became apparent. One student was caught “mooning” a group of others in a common area, and was immediately escorted to the office. His parents were called, and when his mother came to meet with the principal, she swore up and down that her precious son would never do anything like that. It was Principal Blind’s great pleasure, at that moment, to show her video evidence to the contrary.
If you run a school, health care facility, or other business, there’s only one thing you should expect: the unexpected. If crimes are committed, people are injured, or property is damaged or stolen, you may be accused of somehow allowing the transgression to take place. At times like this, the importance of a reliable security camera system cannot be overstated. Conflicting interests and opposing viewpoints can make it almost impossible to determine the truth simply from the oral accounts of witnesses and participants in an incident. However, with a surveillance system recording everything that happens to video, it’s easy to zero in on the time and place of the incident and figure out exactly what happened.
moreWays to Provide Access
As modern facility security systems become more and more sophisticated, businesses and organizations now have a wide variety of options for allowing access to authorized personnel. As Springfield’s trusted security consultant company, Condor Tech wants our clients to understand these different options so that we can help you maintain, install, or upgrade the best integrated security system for your needs. Here are a few examples of the ways in which you can provide building access:
Keypads & Codes
Authorized personnel are given a unique number to input on a keypad at an interior or exterior door. The length of the code could be as few as 4 digits, but shouldn’t be longer than 8 to allow for memorization. Your security system can keep track of what codes are used at which doors, and when they were used. Codes can be easily reset or assigned when needed, making it a fairly easy system to administer.
Keycards
Individuals are given a card to “scan” at the entryway. Depending on the cost, this could either be a barcode that’s read by a laser, a magnetic strip that operates like a credit card, or proximity card that uses radio waves to send a signal to the door’s security interface. In each case, a unique code is associated with each card, so all of the same tracking features are available. One drawback is the possibility of the keycard coming into possession of unauthorized personnel, allowing them all of the same access to your facility.
moreBuilding Security Essentials
Nobody understands the importance of airtight building security better than Springfield’s Condor Tech. For years we have been installing, upgrading, and maintaining building security systems in places where failure is simply not an option. Here is a list of several areas in which you will need to devote attention and resources to make sure your facility is absolutely secure.
Access Points
Doors, windows, fire escapes, and rooftop entryways can all serve as an access point for unauthorized personnel to enter your building. Locks should be maintained and controlled to make sure that only your team members can get through to their specified work areas during specified hours.
Detection
Internal and external lighting should be available to make it easy to detect anybody at night who is in the building or attempting to enter it. A security camera system can also make it easier to detect intruders and provide evidence in the case of a criminal trial.
Reaction
Does your building have an alarm system to alert you and the authorities in the case of an intrusion? What triggers the alarm? Do you have a contingency plan laid out for any type of possible break-in that could occur? These are all important questions that any business or organization should consider.
moreHow We Can Help You
CTS offers integrated security solutions and security systems in Virginia. Twenty years of experience allows us to exceed all expectations with the security solutions we can provide for you. Our goal is to provide you with an efficient and effective system that you can rely on for protection. We truly put you first. If you’re still not convinced, continue reading to see just how we can help you.
- From a design and engineering aspect, we work with you to assess and determine a security system-architecture based on your specific security needs, statement of objectives, and statement of work. We’ll also build and design a system with redundant and continuous operations capabilities. We’ll do this by utilizing both hardwire and wireless communication for ground sensors and mobile units.
- From a project management and assessment standpoint, we’ll always provide up-to-date project status reports to your management group and points of contact. Our program managers will oversee and coordinate management logistics and technical aspects of the security tasks and orders received from you, the client.
- From an installation and implementation standpoint, we offer a fully managed planned installation program of selected products and systems, from planning process to complete installation We make sure each installation is monitored by a team of experts so that it’s completed in a timely and cost efficient manner.
- Once everything is designed to your specific security needs and installed, we’ll make sure that you and your team are 100% trained and that you have constant support from us.
Why Integrate Your Security?
In today’s business world, terms like convergence, synergy and integration are used so frequently that it’s easy to dismiss instances where they actually are occurring. Integrated security systems are a case in point. Behind the growth in security system integration projects is the realization by leaders, managers, school principals, healthcare executives, and more that the risks their organizations face pose catastrophic threats.
Security system integration refers to the trend within a growing number of organizations to merge physical security applications, such as access control, and logical security applications, such as biometric identification programs that allow employees to use the corporate network, into a single, comprehensive system.
There are a number of benefits to integrating the different elements of an organization’s physical and logical security system.
- Firstly, it provides a more comprehensive approach to security that’s less vulnerable to incidents and better able to respond if one occurs.
- An integrated security system also offers the benefit of better protection against the reality that you can perpetrate physical threats logically, and logical threats physically.
Identification, Authentication, and Authorization
Your organization depends on execution of proper employee access in order to maintain effective security of your facility and data. Different members of your staff may have varying levels of clearance depending on their position in your agency. Identification, authentication, and authorization all play a role in granting access to qualified individuals, but the terms are often easily confused. Our security consultants want to help you understand the role that each one serves as an essential piece of your security system. Here is a brief primer to help you discern the difference.
Identification is the process by which an individual claims to be a user on a system or network. Before a user can gain access to a system, they must provide their username, fingerprint, or other identifying information to the system. The system then matches the identifying data with the profile for that user.
During authentication, the system verifies that the user is in fact the person they claim to be. A password or other secret or unique information must be provided to check against the data in the user’s profile. Identification and authentication are easily confused, because both often happen simultaneously. During a standard login, for example, the username identifies the user and the password serves to authenticate them. In the case of a fingerprint scan or other biometric input, the information provided can be used for both identification and authentication.
moreWhat is Integrated Security?
As threats to businesses, organizations, and agencies become ever more sophisticated, the security industry has responded in kind. The term “integrated” is being applied to security systems with greater frequency. You may wonder what it means. At the most fundamental level, integrated security is aimed at addressing the two basic types of threat: physical threats to your building and property, and logical threats to your data and network. Consolidating defenses against both into one department offers opportunities for increased efficiency and innovative solutions.
Protecting against both physical and logical threats means combining your physical and logical security measures. Your network responds to the building’s security system, and vice-versa. Many larger organizations and government agencies are making use of global credentials that allow employees access to both facilities and computer networks. Here are just a few examples of how integrated security is being implemented:
- When an individual gains access to a facility, the system recognizes their authorization and unlocks only the physical areas and computers for which they have clearance.
- Unauthorized entry to the building can trigger the security system to immediately secure the data system from any on-site access.
- A change in someone’s employment status registered in the HR department automatically grants or disallows access to facilities and networks.
- The triggering of an alarm can lock inner doors to seal off areas of your building and/or lock your network down. Depending on the type of alarm, those with higher clearance will still be able to move through the building and access the network.
Our Virginia Security Camera Systems Go Beyond Simple Surveillance
A good security camera system is vital for your Virginia business, but if all you are doing is recording your space while problems occur you aren’t getting the most out of your system. This is how most businesses utilize their security camera systems; they set them up and only refer to the footage after something bad has happened. Condor Tech takes a proactive approach to security footage with our video management and analytics service, helping increase security while reducing loss within your business.
Our technology analyzes your security footage and provides valuable feedback on traffic counts, dwell times, performance tracking, the reduction of false alarms, and more. With our system, you’ll be able to respond immediately to events on your site and send help when needed with a much faster response time. Our system is so powerful it can even help refine your floor plans, supply chain management systems, and more. This is complete control over your facility, and so much more than a simple camera on the wall.
Our security experts are ready to design and install your new camera security system in your business based on your needs and the needs of your business. Then we’ll teach you how to take control of the security of your facility in a proactive, cost-effective way that’s user friendly. Our team will continue to be available for your questions, too, ensuring you are always getting the most from your security system. Give our team a call today or contact us through our website and learn more about our Virginia security camera systems and we’ll get to work on your new system.
moreOur Virginia Security Systems Help You Control Access to Your Facility
For some businesses, putting a deadbolt on the door and a surveillance camera on the wall is all the security system they need. For our customers, their Virgina security systems need to be top-rated systems that help them manage access to their facility 24-hours a day. When customers come to us, they get the cutting-edge technology they need to keep their building, their employees, and their businesses safe. We offer controlled access systems tailored to your needs.
When you decide it’s time to set up a world-class Virginia security system for your building, just give us a call. One of our security experts will visit your site and help you determine what kind of access system is best for your facility. We’ll take into account factors such as:
- Where your business is located
- How much access your employees or customers will need
- The type of business you have
- Your budget for a top-rated security system
Once we have answers to these questions, we’ll match you to a security system that’s perfect for your building. We’ll then install your system and teach you how to use it, so you are confident that the people who need in your building are getting in and everyone else is staying out. This is technology that goes beyond the lock-and-keys of yesterday. Today’s technology will allow you to change access at a moment’s notice and never worry about a lost door key again.
moreIdentifying Suspicious Behavior
While you security professionals are adept at spotting and dealing with suspicious behavior, it can be difficult to keep a vigilant eye on every corner of your business. Even with security camera systems and roaming guards, one of your biggest assets to security is your daily employees. We are not suggesting that they learn to become security experts, but teaching your employees to identify suspicious activity, as well as the proper way to contact security is a skill that anyone can learn.
To help you company remain nimble and secure, it is important to teach your employees including security staff to identify the following suspicious behavior. Should they see something, it is vital that they report it to the professional security personnel according to your predetermined security protocols. If you have not set up security procedures, contact Condor Tech to learn more.
Running
While running doesn’t seem suspicious at first, there is always a reason somebody is running. Do you recognize this person? Do they look scared? Are they looking around as though somebody may be chasing them? The context of the running is important to identifying a threat. Teach employees to ask why they are running.
moreThe 4 Tiers Of Quality Security Systems
Regardless of your location, there is always a chance of a security breach, and without proper planning the intrusion may result in irreplaceable loss of property, monetary loss, or loss of trust with your customers. To help prevent such losses proper security planning and equipment is a must. With over 25 years of security system experience in both the public and private sector, we are able to give advice that makes a difference. By addressing the four tiers of a quality security system, you will be on your way to a robust security plan.
Prevention – Preventing intrusions is the first step in a robust security system. Condor Tech offers a variety of equipment to prevent unwanted visitors, including access control systems, door hardware, and intercom systems. Security booths are also available to add human security that are able to better assess and respond to security issues.
Detection – If someone is able to make it past your intrusion prevention tier, detecting the intruder is of utmost importance. A security camera system allows you to monitor your entrances, exits, corridors, and more in order to detect suspicious activity and obvious intruders. This human detection, coupled with one of our automated intrusion detection systems makes for a thorough detection tier for your security system.
more